TOTP Authentication in KaneAI
Introduction
Teams often need to test SSO or MFA‑protected applications where the second factor is a six‑digit OTP. Native TOTP support in KaneAI generates those codes on the fly from the shared secret key, keeps the entire login journey inside KaneAI with identical behavior in Replay, generated code, and CI, and lets you inject the code directly into your test steps—no external scripts or servers required.
How it works
- Register the TOTP secret once during authoring via Secret Key.
- At runtime KaneAI calculates the correct Time-based OTP code every 30 seconds.
- You can reference the TOPT code as a smart variable inside any test step, assertion, or API call.
Prerequisites
- A TOTP‑compatible login flow (e.g., Google Authenticator, Okta Verify, Microsoft Authenticator).
- The secret key (base32 encoded) associated with the account you want KaneAI to log in as.
Step‑by‑step Guide
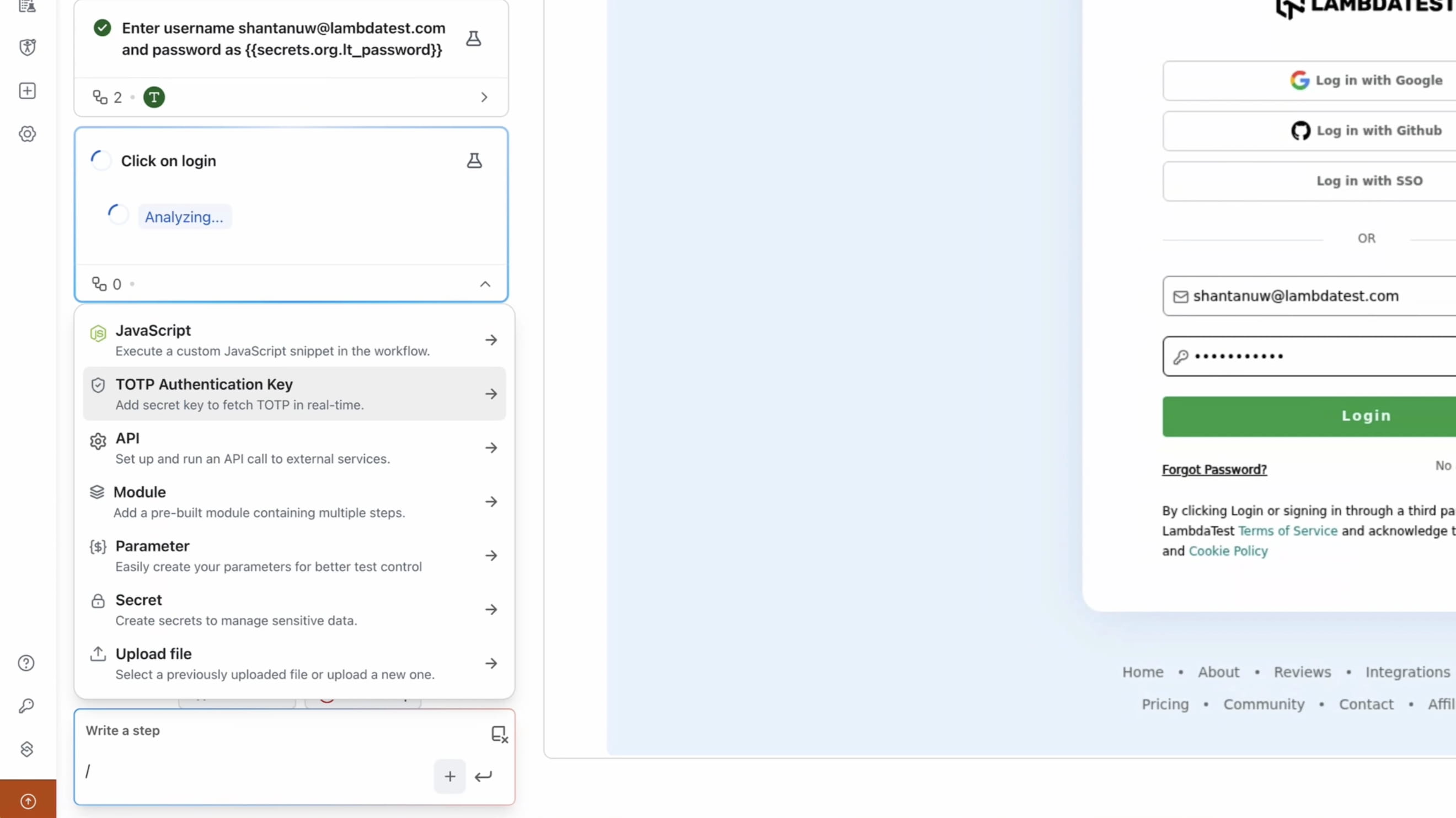
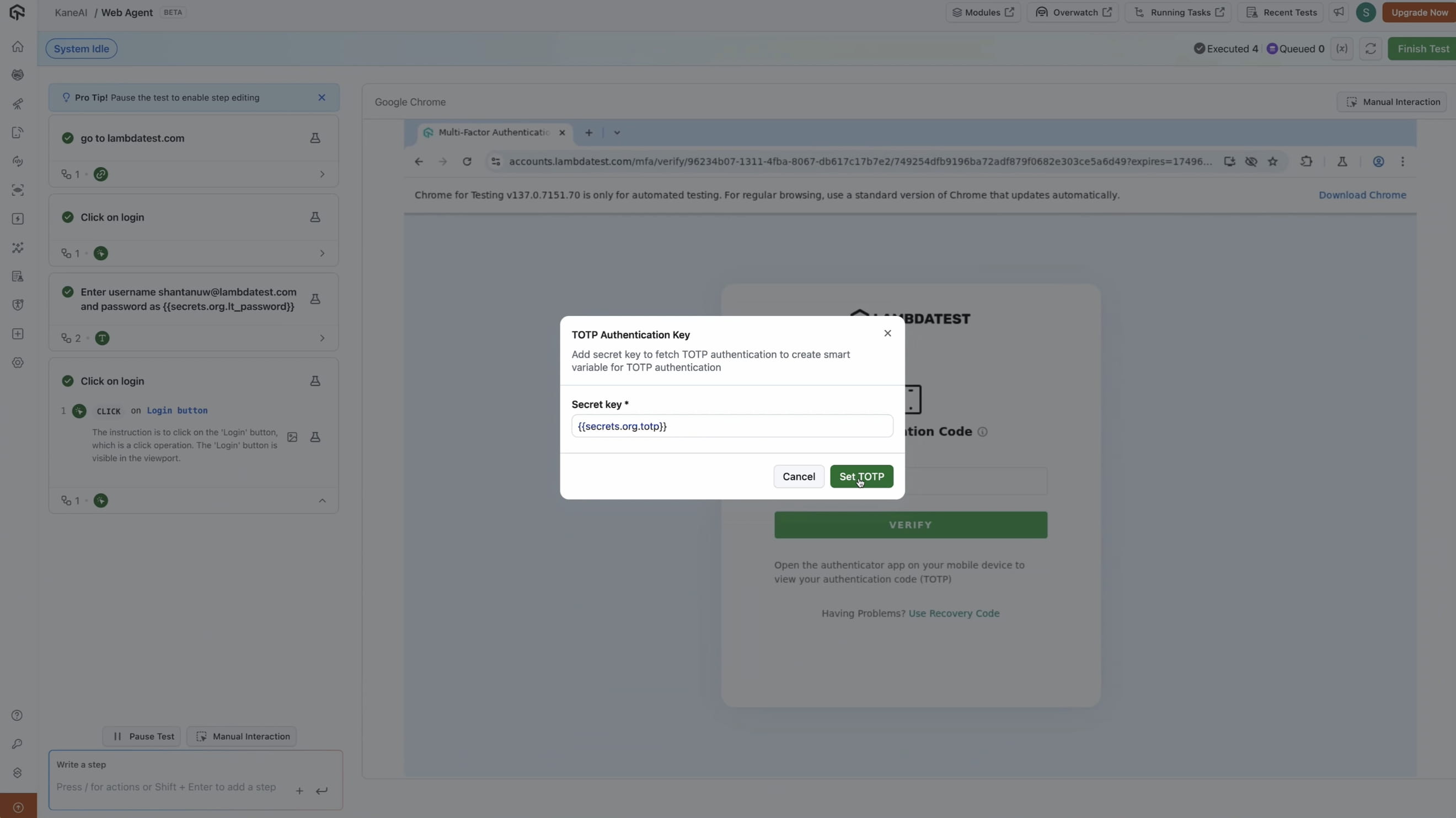
Add a TOTP Secret Key
- Start a web authoring session from here and press /.
- Choose Add TOTP Authentication Key.
- Enter the Base32 secret directly or user TestMu AI Secrets using
{{syntax. - Click Save.
- A smart variable gets generated which provides the 6-digit code based on above secret key when invoked.
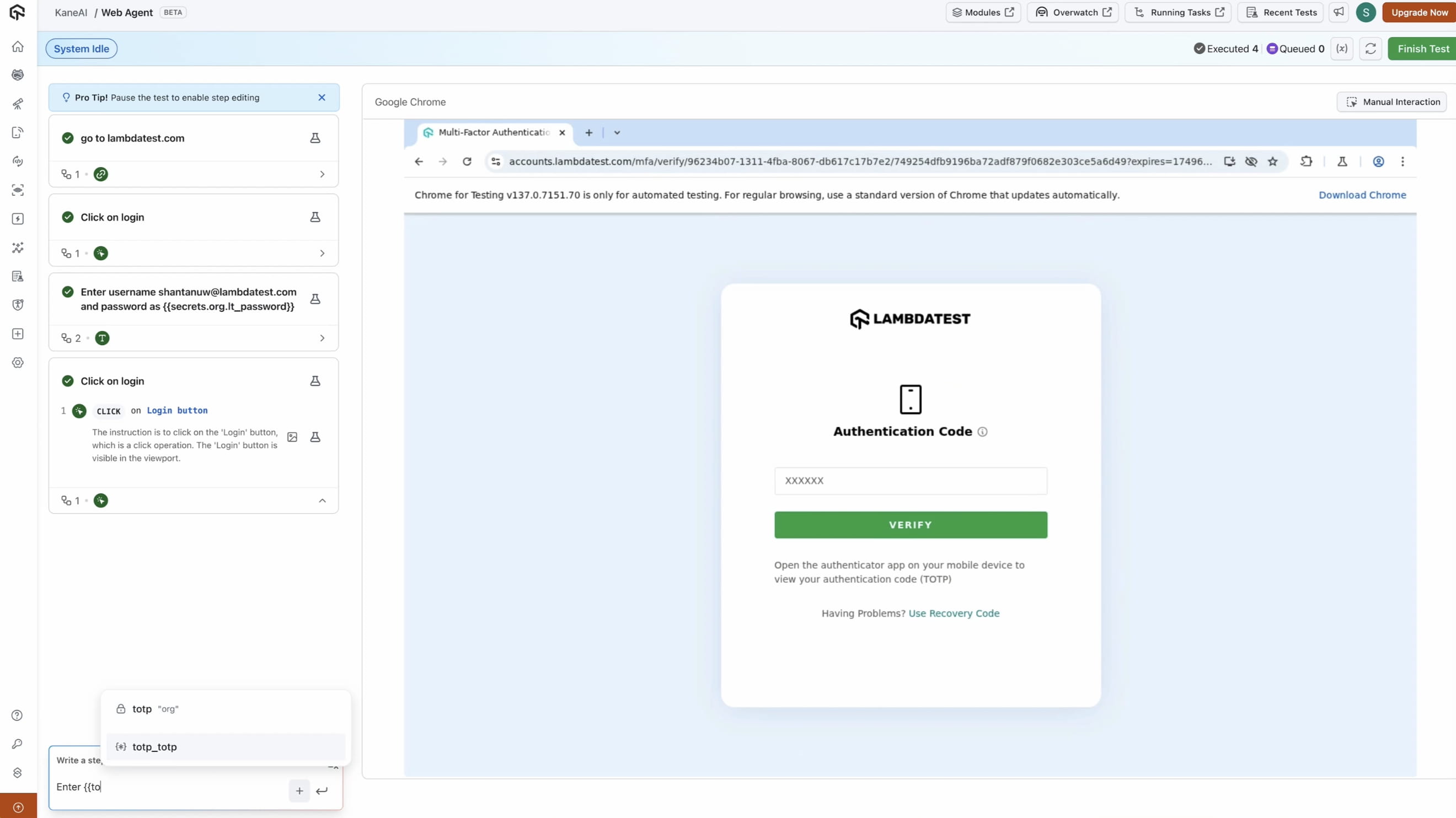
Insert the TOTP into your test
- Navigate to the OTP input field in your application.
- Use the smart variable generated to add your instruction such as "Enter
{{totp}}in verify field" - KaneAI fetches and inserts the 6-digit code.
Video Explanation
FAQ
Does KaneAI store my secret securely?
Yes. Secrets are encrypted, stored in Vault and never exposed in logs or generated code.
Do mobile tests support TOTP?
Yes. The smart variable generated via secret key {{totp}} is available in both Web and Mobile test steps.
