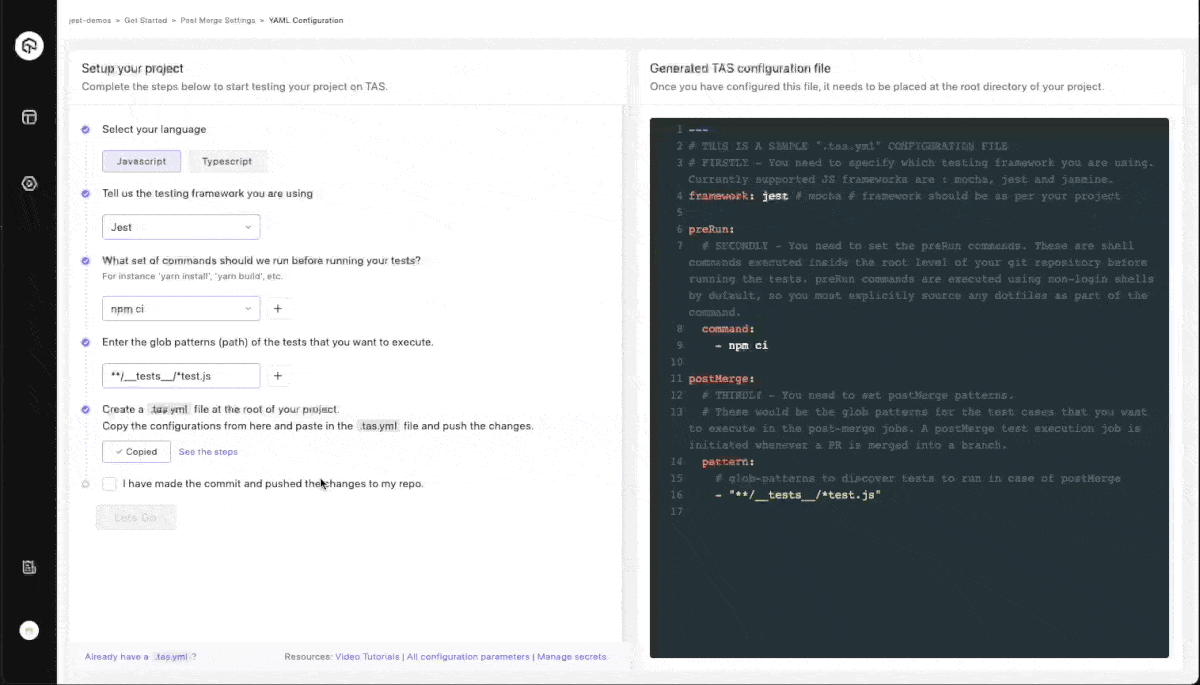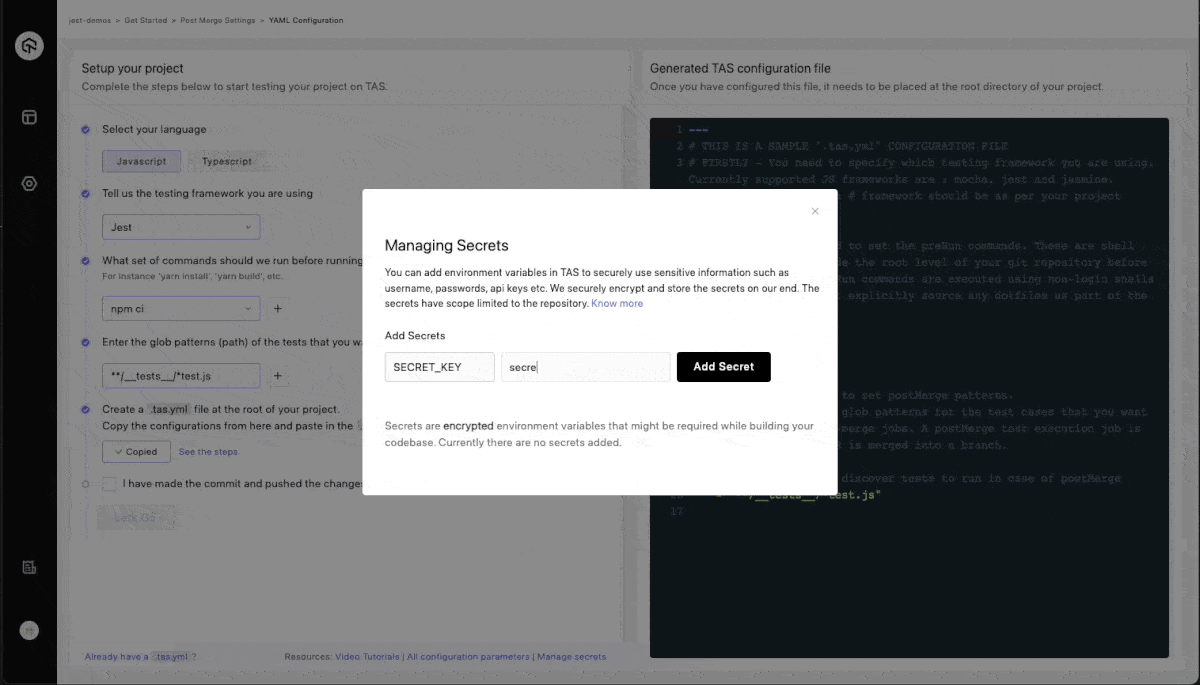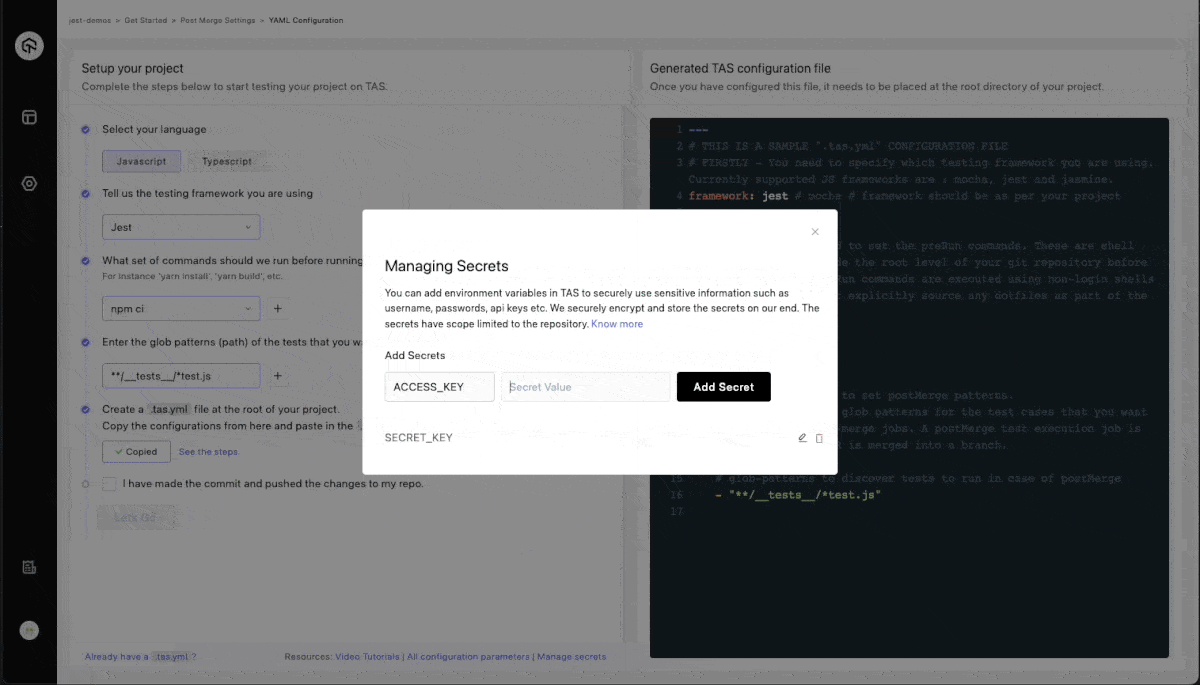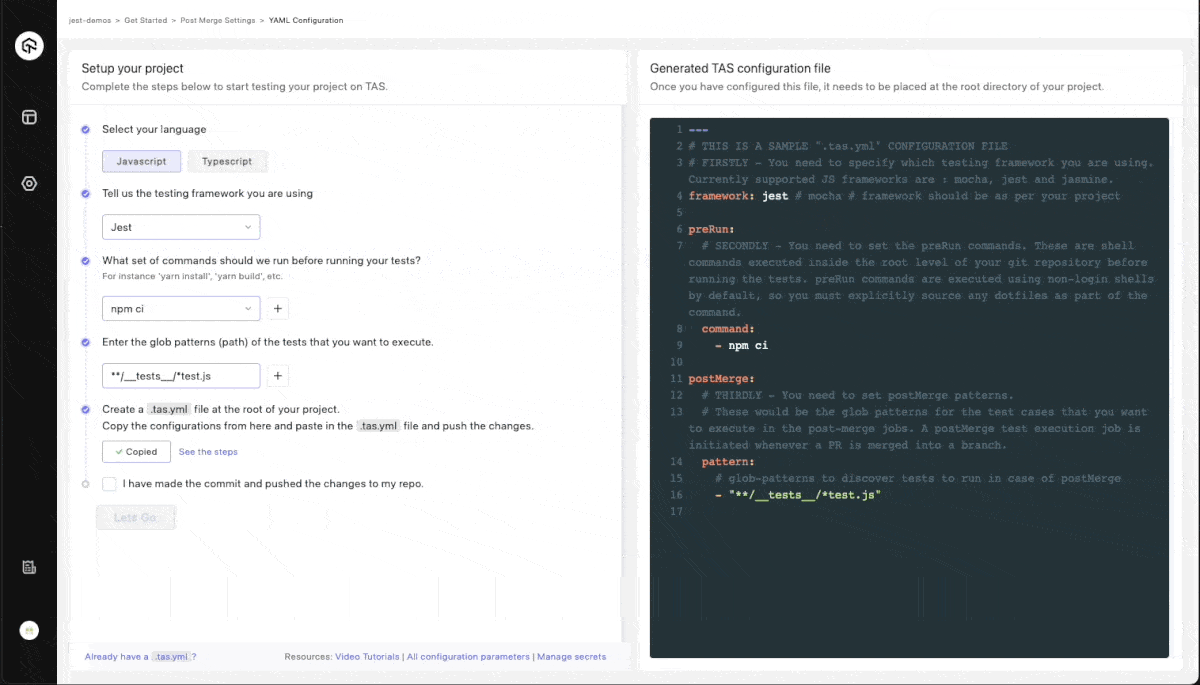
Managing Secrets
You can add environment variables in TAS to securely use sensitive information such as username, passwords, api keys etc. We securely encrypt and store the secrets on our end. The secrets have scope limited to the repository.
Adding secrets for your repository
Adding secrets for the first time - TAS CLOUD
- While configuring .tas.yml
- Click on the
Manage secretsoption located at the bottom - You can add secrets in this section and use them while configuring the
.tas.yml(steps mentioned below.)
Add more secrets - TAS CLOUD
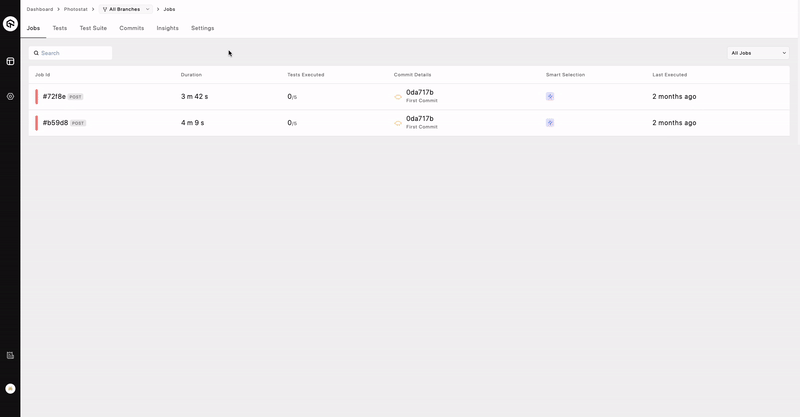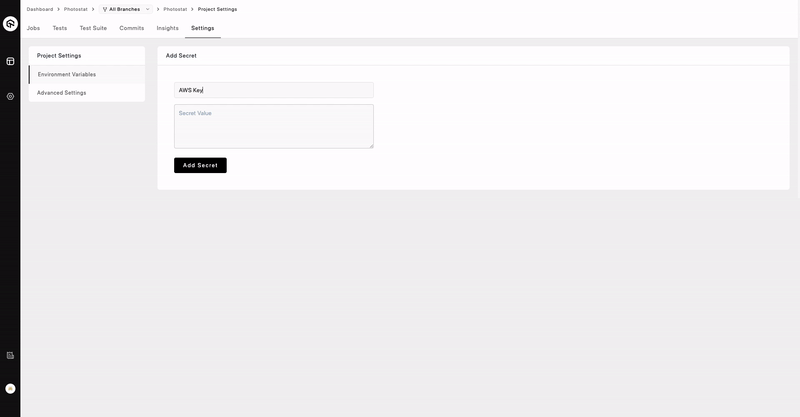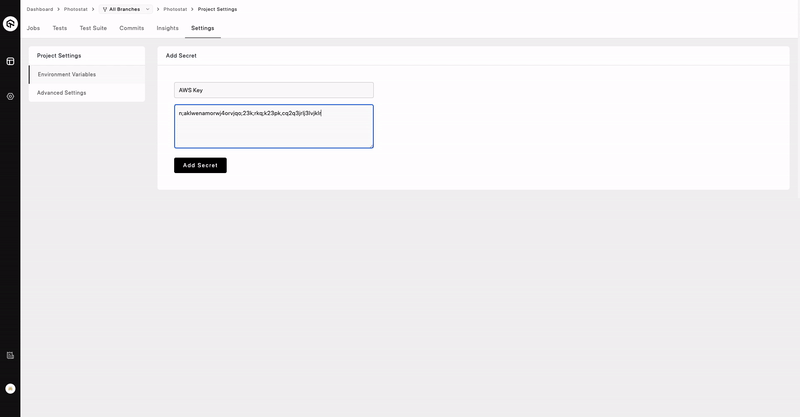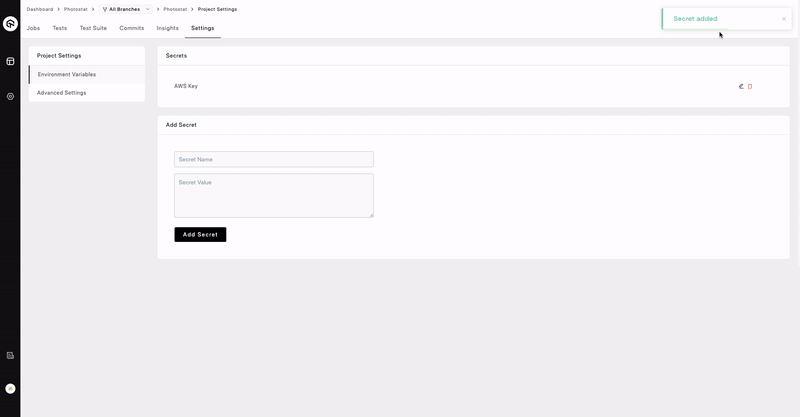
- Open a the repository and navigate to the Settings section.
- Select Environment Variables from the sidebar.
- Add Secret Name, Secret Value and click on Add Secret.
Adding secrets - TAS Self Hosted
- In case of TAS Self Hosted mode, you need to define your secrets in the .synapse.json file. See more details
Using the secrets
- You can use the secrets added in TAS portal inside your
.tas.ymlusing${secret_name}parameter - The following sample file demonstrates how we can refer secrets inside
.tas.yml.
.tas.yml
framework: mocha
blocklist:
- "src/test/api1.js##this is a test-suite"
preRun:
command:
- npm ci
postMerge:
env:
REPONAME: nexe
AWS_KEY: ${{ secrets.AWS_KEY }} #Using secrets inside Yml <--------
pattern:
- "./test/**/*.spec.ts"
preMerge:
pattern:
- "./test/**/*.spec.ts"
postRun:
command:
- node --version
version: 1.0
