Power Your Software Testing with AI and Cloud
Supercharge QA with AI for Faster & Smarter Software Testing

- Web Development
- Home
- /
- Learning Hub
- /
- What Is Static Code Analysis: Techniques and Best Practices
What Is Static Code Analysis: Techniques and Best Practices
Learn what static code analysis is, explore key techniques, and discover best practices to improve code quality, security, and maintainability.
Last Modified on: September 26, 2025
- Share:
Static code analysis inspects source code without executing it, identifying defects, vulnerabilities, and coding standard violations. It detects issues early, reducing debugging costs and preventing technical debt. The process enforces best practices, improves maintainability, and ensures consistency across the codebase. Integrated into development workflows, it provides continuous feedback to developers, helping produce reliable and secure software.
Overview
Static code analysis identifies defects, enforces coding standards, and detects potential security vulnerabilities early in development, reducing technical debt and improving software maintainability and reliability.
What Is the Purpose of Static Code Analysis?
Here are a few benefits of static code analysis, highlighting how it streamlines issue detection, improves code reliability, scales across large codebases, and provides valuable support for developers.
- Early Defect Detection: Identifies uninitialized variables, null pointers, memory leaks, and other coding issues before execution, reducing cost and preventing defect propagation.
- Consistency Across Teams: Enforces coding standards objectively, minimizing subjective reviews and ensuring maintainable, uniform code across large development teams and evolving projects.
- Enhanced Security: Detects vulnerabilities like SQL injection, cross-site scripting, buffer overflows, and unsafe cryptographic usage, strengthening software security before deployment.
- Improved Maintainability: Highlights fragile or defect-prone areas in legacy code, enabling incremental fixes, reducing technical debt, and simplifying future code modifications.
- Integration with CI/CD: Runs automatically on commits or pull requests, providing continuous feedback, maintaining quality at scale, and preventing defects from persisting.
- Objective Developer Feedback: Provides repeatable, unbiased code review insights, enforcing standards consistently, improving overall code quality, and reducing friction between reviewers and developers.
How Static Code Analysis Works?
Static code analysis is a structured process that examines source code without execution, helping teams identify defects, enforce coding standards, and improve overall software quality.
- Select Tools: Choose a static analysis tool compatible with programming languages, scalable for complex projects, integrates with workflows, and encourages consistent adoption by development teams.
- Configure Rules: Establish coding standards aligned with project and industry requirements, focusing on defect prevention, security, maintainability, and actionable, high-impact checks for every scan.
- Scan Code: Analyze source code without execution to identify defects, violations, unsafe coding patterns, and potential vulnerabilities early, before issues can propagate across modules.
- Report Issues: Generate structured reports categorizing defects by severity, with explanations and actionable guidance, enabling developers to efficiently remediate issues and improve future scans.
- Review and Act: Developers address critical defects, adjust rules for future scans, share insights with the team, and reinforce coding best practices consistently.
- Integrate With CI/CD: Embed static analysis into CI/CD pipelines for automatic scanning of every commit, continuous feedback, consistent quality enforcement, and early defect detection.
What Is Static Code Analysis?
Static code analysis is the process of examining your source code without running it. It lets you find potential errors, security risks, or deviations from coding standards early in the development process. Unlike testing that observes how your software behaves when it runs, static analysis focuses on the code structure, syntax, and overall quality of the code itself.
You can leverage tools like linters, static analyzers, or security scanners to identify issues such as uninitialized variables, unreachable code, or potential security vulnerabilities before your code even reaches compilation.
Why Use Static Code Analysis?
Static code analysis core component of static testing that separates teams who constantly react to bugs from those who prevent them proactively.
Here are the benefits of using static code analysis:
- Early Detection of Defects: Static analysis identifies potential defects before the code runs. It flags uninitialized variables, null pointer risks, memory leaks, and other coding issues during software development process. Detecting defects early prevents them from spreading across modules and reduces the cost and effort of fixing them later.
- Consistency Across Teams: Large teams often experience drifting coding styles and inconsistent practices. Static analysis enforces coding standards objectively, reducing the need for subjective manual reviews. This leads to a more uniform codebase, making it easier for new developers to understand and maintain the code.
- Enhanced Security: Many software vulnerabilities stem from coding errors that could have been identified through static analysis. Security-focused tools detect issues such as SQL injection, cross-site scripting, and unsafe cryptographic usage.
- Improved Maintainability: Legacy code often feels fragile because hidden defects make modifications risky. Regular static analysis highlights vulnerable areas, allowing teams to fix defects incrementally. Over time, this reduces technical debt, simplifies future changes, and increases confidence in modifying existing code.
- Integration with Continuous Development: Static analysis integrates smoothly with CI/CD pipelines, automatically running checks on each commit or pull request. This ensures that code quality remains high as the project scales, providing immediate feedback to developers and preventing defects from becoming entrenched.
- Objective Feedback for Developers: Manual code reviews can be subjective. Static analysis offers repeatable, unbiased feedback. This not only improves code quality but also reduces friction between reviewers and developers, since the tool consistently enforces standards and highlights defects.
Note: Test websites and mobile apps across 3000+ environments. Try LambdaTest Now!
What Are the Techniques Used in Static Code Analysis?
Static code analysis examines source code without running it to find errors, bugs, security flaws, and quality problems during development.
The common techniques include:
- Lexical Analysis: Scans source code into tokens, such as keywords, operators, and identifiers. It detects syntax errors, naming inconsistencies, unused variables, redundant code, and insecure hard-coded values.
- Control Flow Analysis: Examines all execution paths to identify unreachable statements, infinite loops, incorrect branching, and missed exception handling. This ensures reliability and improves overall test coverage.
- Data Flow Analysis: Tracks how variables and data move throughout the codebase. It detects uninitialized variables, improper assignments, tainted input, and sensitive data exposure, promoting safe, consistent handling.
- Pattern-Based Analysis: Matches source code against predefined templates to reveal anti-patterns, coding mistakes, or known security vulnerabilities. It enforces best practices, reduces technical debt, and maintains quality.
- Abstract Syntax Tree (AST) Analysis: Represents the code hierarchically to detect structural issues, enforce coding standards, and uncover subtle defects. It also supports automated refactoring and maintenance.
- Symbolic Execution: Simulates execution with symbolic inputs to uncover edge cases, complex bugs, and potential vulnerabilities. It identifies issues that conventional testing techniques might miss.
- Metric-Based Analysis: Evaluates complexity, coupling, cohesion, and maintainability. This highlights defect-prone areas, guides refactoring, prevents technical debt, and tracks enhancements in software quality.
- Formal Verification: Uses mathematical proofs to ensure correctness under all conditions. It detects subtle logic errors or race conditions, ensuring reliability and safety in critical software applications.
How Does Static Code Analysis Work?
Static code analysis ensures teams develop clean, secure, and reliable code throughout the Software Development Life Cycle (SDLC). The process involves a structured approach from tool selection to continuous integration, creating a cycle of ongoing quality improvement.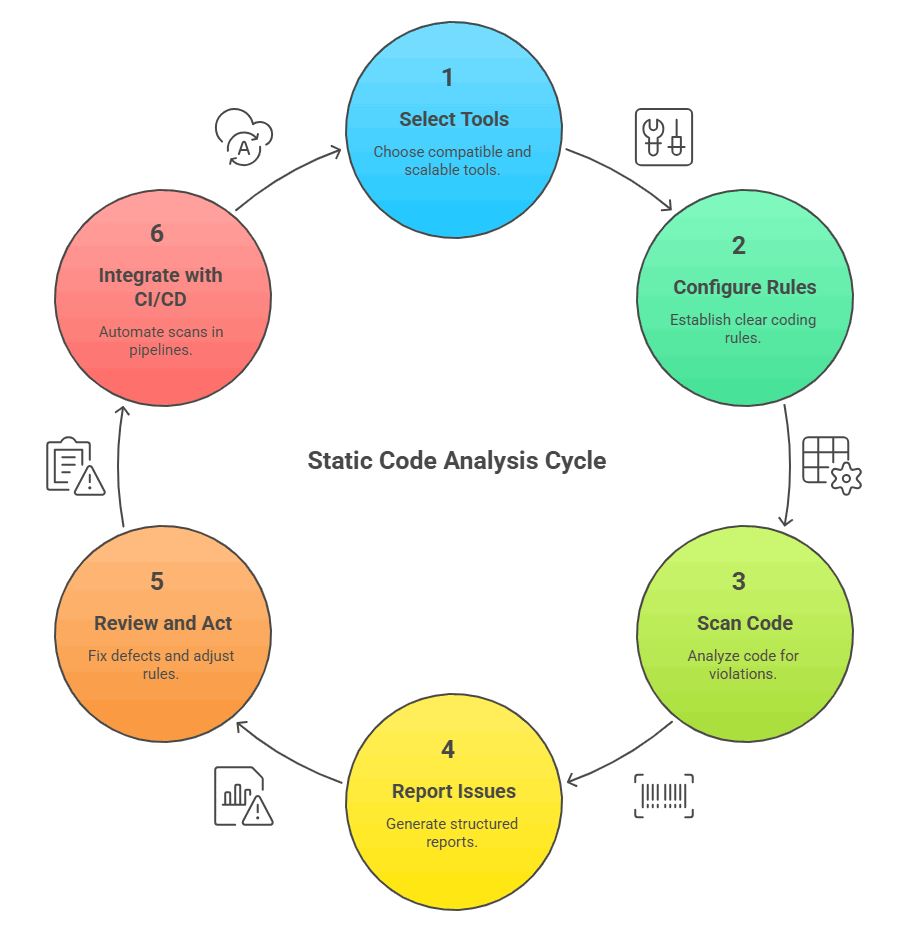
Select Tools
Choosing the right static analysis tool is critical for efficiency and long-term project health. The tool should fit the programming language, integrate smoothly with workflows, and scale as the codebase grows.
- Compatibility: The tool must fully support the programming language and frameworks in use, ensuring accurate and comprehensive analysis. It should avoid the need for workarounds that complicate development.
- Integration: It should integrate naturally with IDEs, build tools, and version control, minimizing disruption to existing processes and developer habits.
- Scalability: The tool must handle growing codebases and increasingly complex projects without performance degradation. This ensures long-term utility.
- Usability: A user-friendly tool encourages adoption, making static analysis a helpful, non-intrusive part of the workflow.
Configure Rules
Before scanning, teams must establish clear coding rules to maintain consistency and reduce defects. Rules should align with project needs and industry standards, focusing on quality and security priorities.
- Standards Alignment: Rules should follow industry best practices or be tailored to the project’s needs, ensuring code is maintainable and reliable. Customization allows flexibility without losing quality.
- Focus Areas: Rules should target code consistency, defect prevention, and security issues, maximizing the value of each scan. This prioritization ensures effort is effective.
- Rule Refinement: Regularly review and adjust rules based on practical findings and team experience, keeping them relevant and actionable over time.
- Manageability: Avoid overly complex or excessive rules that overwhelm developers. Focus on checks that are actionable and impactful.
Scan Code
With rules in place, the code is analyzed file by file without execution. This approach identifies defects and risky patterns before they can propagate or affect other components.
- Violation Detection: The scan highlights code that breaks rules, ensuring consistency and reducing potential defects. Early visibility prevents future complications.
- Defect Identification: Detect issues like uninitialized variables, logic errors, or unsafe operations before they reach production. Early fixes save time and resources.
- Security Pattern Recognition: Identify patterns that could lead to vulnerabilities such as injection risks, unsafe data handling, or improper access control.
- Efficiency: Scanning without executing code saves time and avoids unintended side effects that could complicate debugging.
Report Issues
After scanning, the tool produces a structured report with issues categorized by severity. Clear explanations and actionable guidance help developers in effective defect tracking.
- Severity Categorization: Issues are prioritized by impact, allowing teams to focus on critical defects before less significant warnings appear.
- Explanations: Each issue includes context to help developers understand why it’s a problem and how it affects code functionality or security.
- Guidance: The report often suggests concrete steps to resolve defects, streamlining remediation and reducing guesswork.
- Continuous Improvement: Teams can track recurring issues, refine coding standards, and improve future scans using insights from reports.
Review and Act
Developers examine the report, fixing critical defects and adjusting rules for future scans. This step reinforces good practices and ensures learning from past mistakes.
- Critical Fixes: Address high-priority defects and security vulnerabilities immediately, reducing risk and stabilizing the codebase.
- Rule Adjustment: Modify rules based on non-critical warnings to focus future scans on meaningful issues and reduce noise.
- Team Learning: Discuss findings to reinforce coding best practices and share knowledge across the team.
- Continuous Feedback: Use review insights to enhance code quality and improve the effectiveness of future static analysis.
Integrate With CI/CD
Static analysis is embedded into Continuous Integration And Continuous Delivery(CI/CD) to ensure ongoing quality. Automated scanning for every commit maintains reliability without slowing development.
- Automatic Scans: Every code change or commit is automatically scanned, preventing issues from accumulating and ensuring consistent quality.
- Prevent Escalation: Detect minor defects early before they escalate into larger, more costly problems that affect stability or security.
- Workflow Integration: Fit analysis seamlessly into existing CI/CD processes to maintain velocity while enforcing quality standards.
- Consistent Quality: Continuous checking ensures security and coding standards are consistently applied across the project.
What Are the Best Static Code Analysis Tools?
Developers have lots of static code analysis tools to choose from. These tools find bugs, security issues, and code problems during development. Which tool works best depends on what programming languages you use, how it connects with your current setup, and how your team works.
Here are some of the best static code analysis tools you can use:
- Qodo: It combines static code analysis with AI capabilities to provide deep analysis of pull requests at the component level. It works across various programming languages and supports interactive code review features.
- Snyk: It is a developer-first Static Application Security Testing (SAST) tool that focuses on code vulnerability scanning and auto-remediation. It seamlessly integrates security analysis into the development workflow.
- SonarQube: It is a widely used platform for continuous code quality inspection through automated static code analysis. It supports over 30 programming languages and helps teams identify bugs, vulnerabilities, code smells, and maintain coding standards.
- Codacy: It automates code quality checks and static analysis across many programming languages, evaluating code at every commit and pull request. It promotes early finding and fixing of errors to streamline development.
- ESLint: It is the leading static analysis tool for identifying problematic patterns in JavaScript, TypeScript, and JSX code. It is highly configurable and supports custom rule sets to enforce coding style and quality standards.
- Veracode: It is a comprehensive, cloud-based platform for automated static application security testing. It supports scanning of both source and binary code to uncover security flaws before deployment.
- Coverity: It provides deep, accurate static analysis and SAST for code quality and security. It is scalable for large codebases and integrates with critical development tools to fit into agile workflows.
Furthermore, code review tools build on this foundation by adding a human layer that focuses on architectural decisions, complex logic, and contextual judgment. When integrated properly, these three elements create a continuous, reinforcing feedback loop that improves quality, maintainability, and security.
Challenges of Static Code Analysis
Static code analysis improves code quality but comes with several challenges and limitations that developers must understand.
- False Positives: Tools frequently mark good code as faulty. These can flood developers with useless alerts and make them lose confidence in the analysis. Teams need to spend time adjusting rules to reduce these false alarms.
- False Negatives: Analysis misses real bugs, particularly those requiring runtime conditions or specific user inputs. Since tools only examine code without running it, they cannot catch defects that show up during actual execution or complex system interactions.
- Performance Issues: Large codebases take significant time and computing resources to analyze completely. This can slow down development workflows, especially when tools aren't optimized properly. Incremental scanning helps but doesn't solve the problem entirely.
- Modern Code Challenges: Today's programming languages use dynamic features like reflection, code generation, and heavy templating. These advanced constructs often confuse static analyzers, causing incomplete scans or missed problems.
- Business Logic Gaps: Tools check code structure and syntax, but cannot determine if software meets actual business needs or works correctly for users. Manual reviews and functional testing remain necessary for this validation.
- Setup Complexity: Getting static analysis working properly takes considerable expertise and effort. Writing custom rules, configuring tools, and connecting to build tools creates barriers that can delay implementation and reduce early benefits.
- Incomplete Solution: Static analysis cannot replace other quality methods. It works best alongside manual code reviews, runtime testing, and security audits to provide thorough code quality assurance.
Best Practices for Implementing Static Code Analysis
While static code analysis offers valuable insights, it also comes with challenges and limitations that can impact its effectiveness. Following best practices helps teams overcome these hurdles, ensuring that static analysis is well-integrated into the development process and delivers meaningful, manageable results.
- Integrate Early: Start static code analysis at the beginning of development. Detecting defects early prevents them from escalating into costly or complex issues later.
- Automate Checks: Implement code automation to run static analysis in CI/CD pipelines. Every commit is scanned automatically, catching bugs, vulnerabilities, and code smells consistently.
- Tailor Rules: Configure tool rules to align with your team’s coding standards and project requirements. Regularly review and adjust settings to keep alerts accurate and relevant.
- Prioritize Issues: Focus on high-impact vulnerabilities or major defects first. Minor style warnings and non-critical issues can be addressed afterward.
- Select the Right Tool: Choose analysis tools compatible with your programming languages and development environment. Test detection accuracy and integration effort before adoption.
- Educate and Collaborate: Train your team to interpret reports correctly and encourage collaboration on recurring or complex issues. Shared understanding improves remediation efficiency.
- Combine Approaches: Use static analysis alongside manual code reviews. Tools handle routine bugs, while humans focus on design decisions, architectural concerns, and complex logic issues.
Pro-tip: High code quality ensures software is reliable, maintainable, and secure, but quality alone doesn’t ensure correct behavior. Testing across multiple environments validates that code works consistently under real-world conditions.
Cloud testing platform such as LambdaTest allows you to perform manual and automation testing of websites and mobile applications across multiple browsers, real devices and operating systems. This ensure your website or mobile app work as intended on over different environments.
Conclusion
Static code analysis has become necessary for software testing. It catches bugs, security issues, and coding errors before code runs, which saves time and prevents risks while making code better. Teams that skip this step often face expensive fixes later that could have been avoided easily during development. Static code analysis tools can fit in your build pipelines, giving faster feedback that helps develop software faster and with fewer issues.
One point to note here is that static code analysis doesn't replace other testing approaches, but it catches code issues early in development. This early detection builds developer confidence and prevents bugs from reaching production. When teams combine it with runtime testing and manual reviews, they get complete coverage that protects software quality throughout the entire development cycle.
Citations
- Static Code Analysis Tools - A Systematic Literature Review: https://www.researchgate.net/publication/347383785
Frequently Asked Questions (FAQs)
Did you find this page helpful?
More Related Hubs

Start your journey with LambdaTest
Get 100 minutes of automation test minutes FREE!!